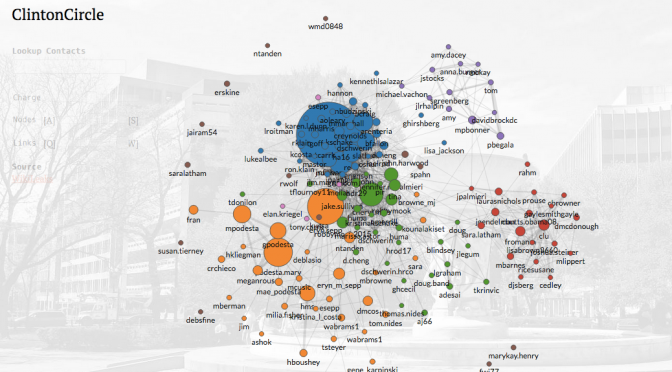
The the MIT Media Lab Macro Connections group created a data visualization tool for the Clinton/Podesta/DNC emails that Wikileaks made available. It is well worth a look. Thanks to Saul for bringing this research to my attention.
Cesar A. Hidalgo, the professor on the project, wrote about what he learned from it. A few quotes stood out for me:
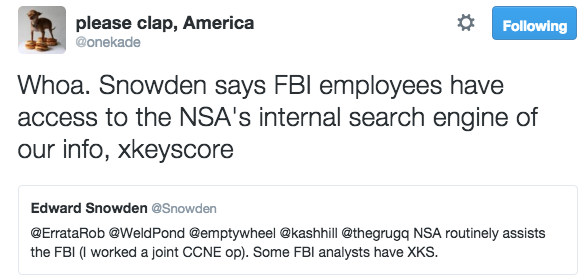
These emails are relevant because Clinton was a person in charge of doing a security job, and anyone working on a security job, is not supposed to communicate using an unsecured or unauthorized channel. This should be obvious, since each extra channel of communication increases the vulnerability of the system by increasing the probability that messages are intercepted. So the reason why Clinton’s emails are a big deal is because a person in charge of security should not be using an unsecure channel, and those who argue from that perspective have a valid point. The fact that the emails were hacked and exposed validates that point.
Which gets to the point we (the Pirate Party) made when the Podesta emails first came out, since, in a sense, we are all in charge of our own security:
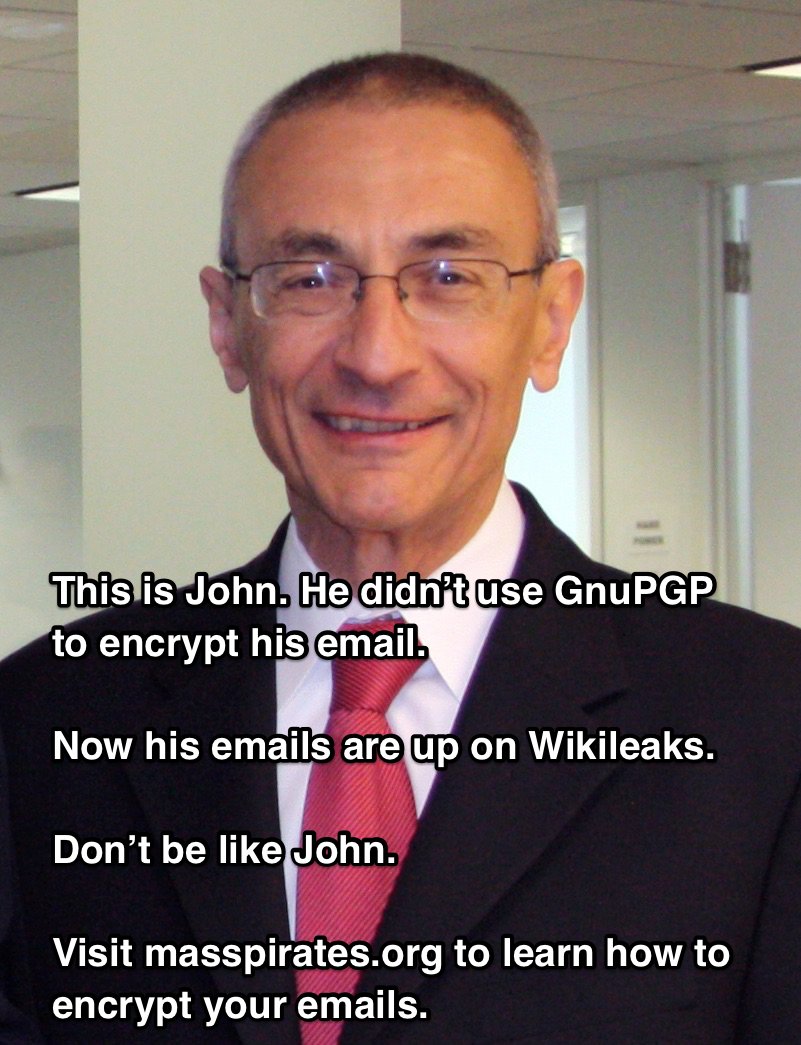
As a Pirate, I found professor Hidalgo’s statement that his motivation for this effort “comes from my support for a society where people have direct access to relevant sources of information through well-designed data visualization tools” aligns well with my own philosophy. We cannot know what our government and our representatives are doing in our name without access to the information they have, presented in a way that people can intelligently make their own assessments of it.
In thinking about how we increase people’s power over our government, I found this statement interesting as well:
So what I got from reading some of Clinton’s email is another piece of evidence confirming my intuition that political systems scale poorly. The most influential actors on them are spending a substantial fraction of their mental capacity thinking about how to communicate, and do not have the bandwidth needed to deal with many incoming messages (the unresponded emails). This is not surprising considering the large number of people they interact with (although this dataset is rather small, I send 8k emails a year and receive 30k. In this dataset Clinton is sending only 2k emails a year).
Our modern political world is one where a few need to interact with many, so they have no time for deep relationships — they physically cannot. So what we are left is with a world of first impressions and public opinion, where the choice of words matter enormously, and becomes central to the job. Yet, the chronic lack of time that comes from having a system where few people govern many, and that leads people to strategize every word is not Clinton’s fault. It is just a bug that affects all modern political systems, which are Ancient Greek democracies that were not designed to deal with hundreds of millions of people.
In my mind the solution to this issue is to setup systems so that people are able to make more decisions about government. Not faulty marketplace democracy with its one dollar one vote, but true democracy of one person one vote. Proportional representation instead of winner take all elections. Sadly, I find many adherents of the two old political parties don’t get this. We have a long road to travel until we get there, but we will.